The global health sector has become a highly attractive target for cyber-attacks. Since 2017, a substantial increase has been reported in the number of attacks against entities in the sector and those indirectly related to it (IDB, 2021).
Increasing risk in the health sector
The target for cyber-attacks has varied throughout the supply chain, from health service providers directly to pharmaceutical companies and suppliers of goods and services associated with the sector.
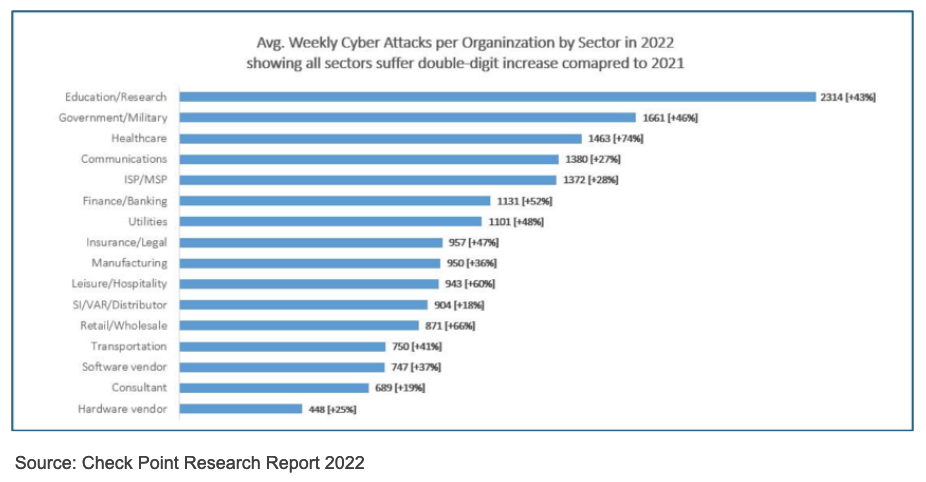
Figure 1 shows the number of weekly attacks on each sector during 2022. It is notorious the health sector occupies fifth place, with 1,387 attacks on average per week. However, when analyzing the increase in attacks compared to the previous year, it is shown that the numbers for the health sector grew the most, with an increase of 69% in attacks. This trend has continued in recent years, and if it remains, by 2026 the health sector will be the main target of cyber-attacks globally.
Given this trend, it is not random that, according to a study conducted by Trend Micro at the end of 2022, 77% of health sector companies consider that they will be subject to a successful cyber-attack in the next 12 months.
Why are cyber-attacks increasing?
When analyzing the above outlook, and demonstrating [PL1] the imminent risk in cybersecurity threats to the health sector, the question that arises is, why is this sector so attractive for cyber-attacks? The answer to this has different causes that have become catalysts for this sector to become a highly profitable target for cybercriminals (Swivel Secure, 2022).
- Private client information: The health sector is one of the sectors concentrating the most confidential personal information in their databases. Such information is undoubtedly an asset of great value and easy sale by cybercriminals.
- Easy access point: The level of protection, in terms of Cybersecurity, of the health sector is low compared to other sectors also concentrating big amounts of information.
- The need for remote access: Due to the accelerated digitalization processes experienced during the pandemic, the number users of health platforms have increased; while organizations have not developed at the same pace protocols and standards to hold back numerous cyber-attack strategies.
- Protection vs easy access: In their desire to facilitate access to digital service channels, health sector entities have been forced to sacrifice their level of protection.
- Lack of corporate education: Health personnel have a very diverse professional background, causing difficulty in successfully implementing corporate education programs for information security.
- Very broad cyber network: The health sector is introducing new technological systems without acquiring cybersecurity systems.
- Parameterization of information: The organization of information required by the sector to facilitate interaction between various actors in daily work, makes such information very desirable in the cybercriminal market.
Implications and costs for the health sector
The relevance of cybersecurity in the health sector has been relegated by physical security and other priorities in recent years (Verizon, 2022), which has increased the severity of the impact of each attack suffered. In addition, the process of forced adoption of cyberspace during the pandemic generated the acquisition of cyber capabilities at a surprising speed, without them being backed by a cybersecurity system. This led to increased dependence on digital media without guaranteeing its continuity towards possible threats.
As established by the IDB (2021), the approximate cost of a Cyber-attack to the health sector is US$10.1 million, while the same attack in other sectors has a cost of US $3.9 million.
This difference in the economic impact of a cyber-attack on the health sector is explained by several factors:
- The lack of investment in cybersecurity and, above all, in cybersecurity.
- The various damages caused by the attacks in the health sector have not only directly quantifiable repercussions, but also other far-reaching effects (Trend Micro, 2023).
- The interruption or damage to critical infrastructure, translates into a reduction in the profits related to the service provided, medicines sold, or patents infringed.
- The decreased productivity during and after an attack is a factor to consider. The average number of days between an incident and its identification in the health sector is 329 days. (IDB, 2021)
- There are costs that go beyond the economic sphere, such as reputational damage suffered by an organization when its ability to shield its customers’ private data is questioned.
- Judicial lawsuits and regulatory actions brought by clients and key actors before organizations or institutions.
Challenges and Threats 2023
Considering the trend of increased cyberattacks against the health sector, and analyzing the modus operandi of the cases that occurred in previous years, four main threats in cybersecurity can be identified by 2023:
-
Phishing
This type of attack is the most common one facing the health sector, as well as being the most successful. It consists of an email, text message, link, or other type of communication channel in which they impersonate an institution or individual with the aim of the victim providing personal information or access credentials. Through this, they usually access private information or business systems from which they can expand the impact of the attack and give way to other strategies.
-
Ransomware
This type of attack is one of the most emblematic against the health sector in recent years, especially in Colombia. Here, the attacker seeks to access private information from an institution’s databases and encrypt it to prevent its use by the institution. Then they demand an economic ransom to release the information.
-
Data Breaches
This attack commonly arises from a successful phishing and aims to penetrate the systems of an institution. Unlike ransomware, they do not seek to encrypt and request a ransom, but to access and possess full use of the platforms, tools, and information of the victim institution.
-
Denial of Service
This mechanism seeks to overload the digital systems of an institution to hinder the continuity of the service offered. As supply chains increasingly depend on digital processes, a cyber-attack that denies operational functioning can have a profound impact on the health sector.
Companies generally face challenges at three different levels to face the threats explained above: (Trend Micro, 2023).
The first level is people and their knowledge on the subject, the lack of knowledge of senior management of companies about cybersecurity and its prioritization in risk analysis, has slowed the adoption of capabilities to increase prevention and resilience to possible attacks.
The second level are the improvements in processes, meaning protocols and roadmaps previously established to face the imminent cyber-attacks.
The last level responds to the technical and technological capabilities to respond to an incident of this nature. In most cases companies outsource much of their cybersecurity system without tracking or monitoring their status, and even on many occasions they do not even have the tools available to defend themselves.
In short, although the health sector has great challenges and risks in cybersecurity, it has clearly identified aspects to design a roadmap to effectively manage those risks:
- Raise investment in cybersecurity and cyber resilience tools.
- Enhance mechanisms of awareness from the managerial level to the end users in the sector.
- Acknowledge the best meeting point between information protection and easy access to service end-users.
- Strong mechanisms to merge information between different health sector organizations and entities, to be able to share data regarding threats, attacks and lessons learned.
References
Checkpoint Research. (2023). Cyberattacks on the Health Sector Report 2022.
Kost, E. (March 31, 2023). Biggest Cyber Threats in Healthcare. UpGuard Security.
SonicWall. (2023).2023 SonicWall Cyber Threat Report.
Swivel Secure. (2022). 9 Reasons Why Healthcare is the Biggest Target for Cyberattacks.
Tejerina, L. and Paz, S. (February 22, 2021).The health sector is the most attractive for cyber attacks. Are we prepared to protect it?. Inter-American Development Bank.
Trend Micro. (2023). Trend Micro Cyber Risk Index (CRI) 2H´2022.
Verizon. (2022). Data Breach Investigations Report 2022.
