Cities can create safer, more efficient, and resilient communities through technological innovation and data-driven decision making; However, these opportunities can also bring potential vulnerabilities, impacting national security, citizen safety, and critical infrastructure operations.
THE CITIES: A DIGITAL ECOSYSTEM
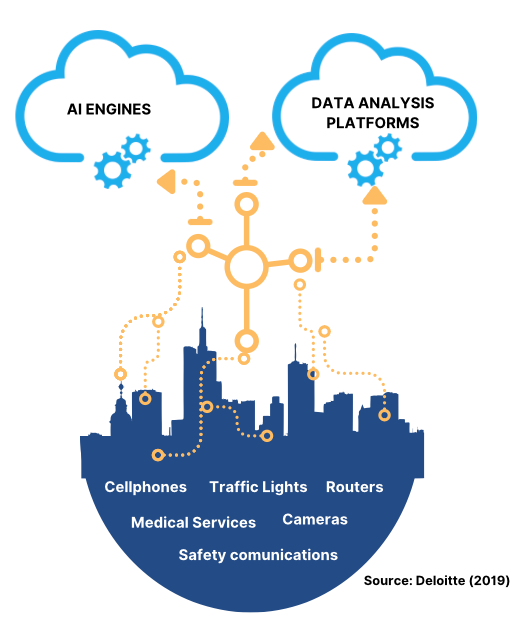
Cities have become a complex ecosystem of municipal services, public and private entities, people, processes, devices, and infrastructure constantly interacting with each other. In general, it is possible to identify 3 layers within this system:
THE CORE
The core is the technology platform (cloud platform, IOT data platform – Internet of Things) processes data and generates the market logic to give meaning to the data flowing from the perimeter.
THE COMMUNICATION LAYER
The communication channel (Bluetooth, NFC, LTE. WIFI Direct) establishes a constant and bidirectional data exchange between the various components of the ecosystem.
THE EDGE
The edge layer comprises devices like sensors, actuators, and smartphones, as well as IOT applications such as smart lighting and smart waste collection. These are the front lines of smart cities.
Key Actors in the Cybersecurity Process
Government Leaders
Municipal Managers
Information technology personnel and third parties
In addition, to become a Cyber Safe City, the ecosystem must comprise the following:
- Citizenship as recipient of the services.
- Platforms and communications networks to allow proper delivery of information.
- Connected devices, applications, data, and the information they transmit.
- An urban ecosystem through which public services are provided.
- The technological infrastructure and the systems supporting the provision of digital services.
- Cybersecurity capacity to protect assets. An authority taking care of all previous elements.
Source: IDB (2021)
Why is it important to design cybersecurity mechanisms in cities?
- Helps cities and local administrations to protect themselves in cyberspace.
- Increases awareness and understanding of cybersecurity, in a growing digital environment, as well as the connection of urban infrastructures and services.
- Reduces risks in the data exchange processes between users and public and private entities, in addition to the protection of their physical infrastructures.
- Fosters an environment enabling economic growth and the development of cities.
- Prevents urban chaos. A cyber-attack affecting traffic, public transportation or emergency services could result in the collapse of flow of people and goods within the city.
Cities must develop a holistic approach for physical and digital infrastructure, enabling interoperability and interconnection, while providing safe spaces for users and data managers.
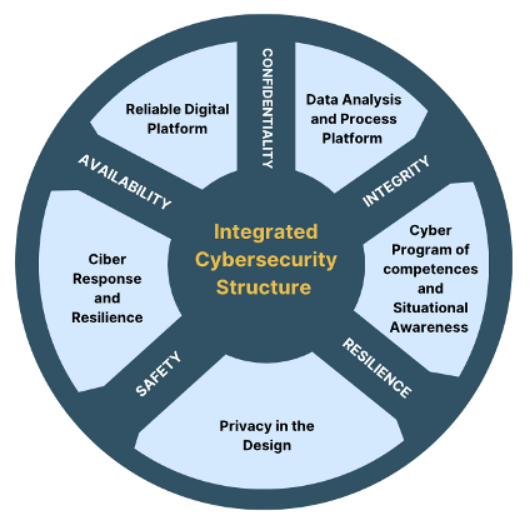
Smart City Security objectives: Confidentiality, Integrity, Availability, Safety and Resilience must be based on the objectives of traditional information technologies (to protect data) as well as operational technology (to ensure security and resilience of systems and processes). These combined security goals can help cities maintain a safer and more resilient operating environment.
Motivations for a cyber-attack on cities
Personal
The attacker seeks to satisfy a desire, meet a challenge, curiosity, revenge, or personal satisfaction.
Business (unfair competition)
Endangerment of information, obtaining corporate secrets, knowledge of the business activity, the infrastructure supporting services and, in general, the goods or services offered.
Criminals
Criminal motivation can be linked to two purposes. To damage, injury, or endangerment of the victim’s legal assets; or, to obtain benefits for the perpetrator or a third party.
Economic
The materialization of an attack may seek retribution, compensation, benefit or gain for the attacker or a third party.
Politicians
Change of the prevailing political regime, the fall of a democratic sector, the direction for making a citizen decision, the endangerment or destabilization of the sovereignty, government, territory, or population of a nation.
Others
There are other motivations or a set of different motivations in the same vulnerability event. For example, a criminal activity may be carried out due to revenge and at the same time, have economic or corporate competition motivations.
Consequences of cyber-attacks on Cities
- Disruption of critical city services, such as energy, water supply/treatment, mobility, health, traffic control, etc.
- Reduction in worker productivity, including the cessation of collection of municipal revenues.
- Impossibility of providing services to citizens, such as carrying out procedures or issuing authorizations, among others.
- Damage of reputation of the municipal administration and distrust.
- Violation of privacy and data confidentiality laws, which may lead to investigations and sanctions.
- Loss of investments carried out to provide services.
- Political, economic, or social destabilization.
- Impact the integrity, availability, confidentiality and authenticity of the data.
How to reduce cybersecurity risks in cities?
The Cybersecurity and Infrastructure Agency (CISA) and the National Security Agency (NSA) of USA, in their annual decalogue of recommendations (2023), included a series of elements for decision makers in cities to consider when formulating a public cybersecurity policy, among which are:
- Include strategic foresight and proactive cybersecurity risk management processes in your plans and designs to integrate smart city technologies into your infrastructure systems.
- Apply the Principle of Least Privilege (PoLP) in all your network environments. As defined by the US National Institute of Standards and Technology (NIST), the Principle of Least Privilege is a fundamental concept in cybersecurity and access control that advocates for granting individuals or systems the minimum level of access necessary to perform their assigned tasks.
- Secure remote access applications and enforce multi-factor authentication (MFA) on local and remote accounts and devices where possible to strengthen the infrastructure that enables access to networks and systems.
- Implementing zero trust network design principles will create a more secure network environment that requires authentication and authorization for every new connection with a layered security and defense-in-depth approach.
Success stories
Singapore
- A unique case as it is essentially a City-State.
- Successful model for implementing public policy, replicable for other cities.
- High accessibility to the Internet by the population, with a highly developed level of technology and digitalization, involving a massive amount of data, integration of the Internet of Things (IoT) and interoperability of the various services offered to the population (IMD, 2023).
- Sensitivity and vulnerability to cyber threats is proportionally greater than that of other cities in the world.
Strategy
- Infrastructure: Construction of a cyber resilience infrastructure through the compartmentalization of municipal units, investment in their defenses and identification of the critical infrastructure located at the center of the security strategy.
- Prevention education: Considering the omnipresence of cyberspace, efforts are aimed at making this a safer environment through a policy of raising awareness and educating the population on security protocols and constant surveillance of cyberspace to activate technical capabilities preventively.
- Regional cooperation: Adoption of a cyber cooperation approach at the regional and global level.
The Hague – Netherlands
- The Hague was one of the first Smart Cities to adopt resilience scope in contrast with the utopian aspiration of cyber immunity which various cities around the world pursued without success. (Deloitte, 2019).
- Cybersecurity as a cross factor in the general decision-making process of municipalities and cities, as procurement, evaluation, and other processes to enable a coherent public policy execution protecting the integrity of information and processes.
Strategy
- Acquire cyber resilience through five pillars of the NIST framework: 1) Identify, 2) Protect, 3) Detect, 4) Respond, 5) Recover.
- Establish cybersecurity protocols in diverse levels and stakeholders: Strategic: City Hall, Tactic: Departments and secretariats, Operative: Workers /employees.
- An example of this is that at least five of the internal information security departments have an additional role of advising and counseling at the strategic level.
- This, more dynamic strategy, preventive and innovative in the city allowed its cybersecurity capacity to expand without hindering the digitization process.
Tel Aviv – ISRAEL
- Tel Aviv is a city that prioritized its security at a general level given its geopolitical context (Israel National Cyber Directorate, 2021).
- A city with rapid digitalization largely due to the factor of digital and technological companies in the national economy. It has multiple startups and leading companies that promote a constant and innovative ecosystem in cybersecurity.
- Due to numerous cyberattacks throughout the critical infrastructure and anticipating that they will continue to increase, Tel Aviv decided to implement its own cybersecurity strategy aligned with the national cybersecurity strategy, with rapid deployment against local threats.
Strategy
Two-level cybersecurity policy: Strategic and cooperative.
- The strategic level is aligned with the action model of the National Cyber Directorate, which allows a local response in everyday cases, but in the event of state or high-impact threats, functions are temporarily transferred to the state level.
- At the cooperative level, various actors in the cyber sector are proactively involved in preventive planning and promoting cyber resilience.
Tokyo – Japan
- Tokyo stands out as one of the most technological places in the world. Industry-leading companies such as Panasonic, Sharp, Mitsubishi and others are dedicated to working hard to make the city a benchmark for smart urbanization.
- The presence of NFC technology throughout the city is crucial for the development of daily life activities. All public transport in major Japanese cities can be paid with NFC and thousands of kiosks, convenience stores and large stores receive payments by this means.
- It has rapid communication services and a wide range of alerts through mobile phones in case of contingencies such as earthquakes.
Strategy
- In 2022, Japan published two important security-related documents: The Cybersecurity Policy for the Protection of Critical Infrastructures (CPCIP) published in June by the Strategic Cybersecurity Headquarters, an entity headed by the Chief Cabinet Secretary) and a Cybersecurity Strategy. National Security (NSS) revised. (December).
- The CPCIP will help critical infrastructure operators to further promote responses at all levels of organizations. The NSS, a more comprehensive document that outlines the country’s need to strengthen its cybersecurity response capabilities and adopt cutting-edge cybersecurity-related practices and technologies.
References
Deloitte (2019). Making smart cities cybersecure.
NSA (2023). Cibersecurity Best practicies fo smart cities.
IDB (2021). Cybersecurity guide for smart cities.
www.technologyreview.com
Burbano, L. (2023, May 31). Cyber Resilience, Pillars and Examples of Cities that Apply Them. Tomorrow City.
Cyber Security Agency of Singapore. (2021). The Singapore Cybersecurity Strategy.
Deloitte. (2019). Making Smart Cities Cybersecure.
IMD. (2023). Smart City Index 2023.
Israel National Cyber Directorate. (2021). Israel International Cyber Strategy – International Engagement for GlobalResilience.
Mims, Christopher (2011). Cellular Technology that Told Japan an Earthquake Was Coming. MIT Tech review.
